Many websites depend on one-time password (OTP) verification to fight fraud and ensure contactability in their account sign-up workflows. More sophisticated platforms may use static metadata about phones, such as line type, to block bad actors. Fraudsters have found new ways to acquire more standard phone numbers where static information looks like a real phone number. These phone numbers are usually shared, thus the only way to catch the fraudsters is to examine the phone number’s usage across many websites.
Fraudster Story
ACME’s new digital promotion, for example, gives each new user a $20 gift card. ACME requires the new user to verify their phone number and email address with OTP. But ACME is advanced and even checks the line type of the phone. Non-fixed VOIP phone numbers, for example, can be spun up in minutes without requiring any sort of user verification. ACME has seen abuse associated with this type of phone number in the past, so the $20 gift card will not be rewarded to users who register with a non-fixed VOIP. One point for ACME.
When Rules Work
A fraudster sees this generous offer and creates accounts with fake identities to get several gift cards. On the first try, the fraudster sets up an account using a TextNow phone number but notices he is not awarded the gift card. One point for ACME.
The Fraudster Finds a Leak
The fraudster tries again. He Googles, “how to receive text verification for free” and find an article listing several sites that do just that. He visits SMS-Online and uses one of the numbers published. The fraudster can’t send messages but can receive one-time passcodes, and more so, these numbers are registered to a big four carrier. He grabs one of the numbers, sets up an account, and is rewarded with a $20 gift card. One point for the fraudster.
The fraudster looks for more of these sites and replicates, getting hundreds of dollars in free promos. One hundred points for the fraudster.
Missing the Fraud
The site that the fraudster used actually buys sim cards, registers numbers, and attaches them to a modem. The owner of the website publishes the messages received on the phone. Because it’s a mobile number, it gets through the “phone line type” filter that is popular among Ekata’s customer base. A blacklist could work, but would be outdated quickly, and it turns out many of these websites remove phone numbers after 30 days.
How to Stop the Fraud
Ekata is uniquely positioned to catch this type of fraud. The bad news for fraudsters is that these numbers are shared, so they are very likely to hit the Ekata Identity Network several times in a short period with many different digital identities.
Ekata identified this trend, took the time to gather several hundred phone numbers from many different websites and observed how these phone numbers behaved in the network. We saw that when a phone number appeared on the website, it began showing up in the Ekata Identity Network several times per day, but always with different identity combinations. The Network Score immediately jumped higher.
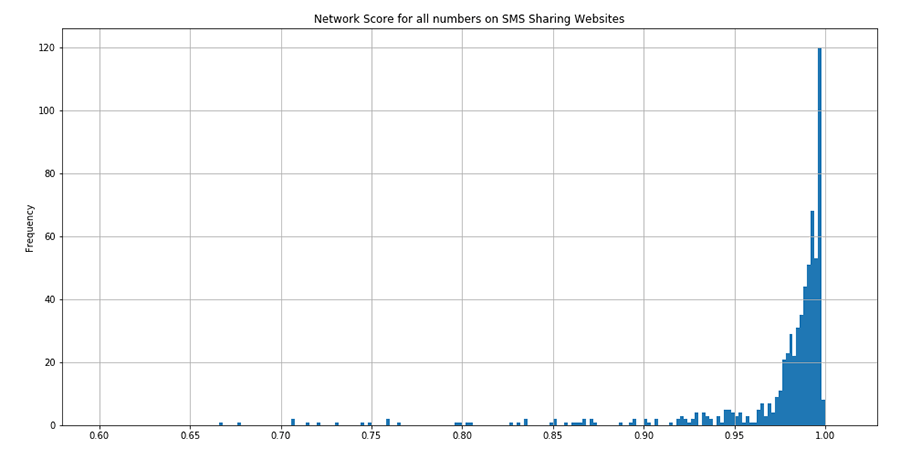
If ACME had written a rule around Network Score, it would have captured 88% of all the attempted fraud, but only impacted 2% of the new sign-ups. Furthermore, there are likely other Network Signals that might be useful, should they be surfaced, to catch this type of fraud.



