Welcome to Ekata’s Executive Series. In this series, our CEO, Rob Eleveld, will be outlining the dynamics we see developing in the global identity verification (IDV) market and highlight Ekata’s response to continuous market demands. Today, we are digging into the deterministic approach of credit risk and comparing it to the probabilistic approach of fraud risk.
One word. Trust.
So hard to build and so easy to break! During my formative years of professional development, I served as a submarine officer in the United States Navy. Trust and integrity were the name of the game. Today, as CEO of EKATA, trust is still what I value most; in leadership, in hiring, and in any and all product development.
In the global ecosystem of payments, lending, and eCommerce specifically, the term “trusted data” comes up often. This is a loaded term and it can mean different things to different people in this business.
Allow me to humor you as I begin our discussion into trusted data with a brief story…
A Vignette: An Executive Briefing and a Question of Trust
As CEO, one of my duties is to provide high-level briefings to key executive customers, partners, and prospects around the world. I truly enjoy doing these in person and look forward to starting up again and logging off Zoom when it is safe to do so.
In a meeting with a veteran payment executive, I was showing the curve below. I always show this curve because it very clearly displays what Ekata does, but more importantly, what we do not do.
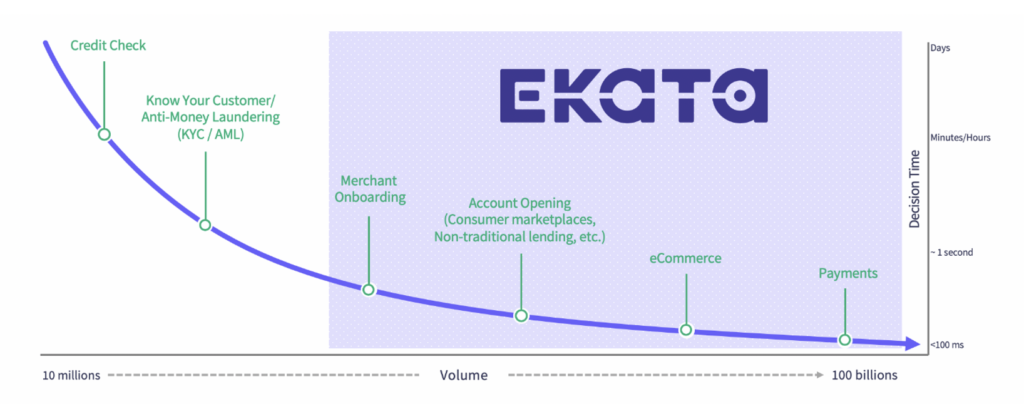
We do not provide credit risk or KYC/AML solutions or “static personally identifiable information” (static PII) data elements (SSN, date-of-birth). Instead, we focus on digital identity verification for risk management on new account openings, account integrity/takeover, and payment authentication and transactions with “dynamic PII” (name match with email, phone, address, and IP).
This executive loved the slide. Mission accomplished, I figured; we had conveyed exactly what I wanted to “without words” to an industry veteran.
But then he asked, “Do you intend to shade Ekata’s offerings over to the left at all, more towards KYC/AML or credit? Because then your data would be more trusted.”
That statement brought me up and out of my chair! Everything we do here at Ekata is about trusted data. We continued our conversation and focused it on the key differences between credit risk and fraud risk.
Here are the takeaways from our conversation.
Trusted Data Starts at the Source
Ekata has been sourcing domestic U.S. identity data for more than a decade. More importantly, we have been sourcing global data since 2015. Our global network of consultants has referred hundreds of sources to us; yet due to our very stringent and rigorous vetting and testing requirements, we evaluate about 25% of those and only one out of ten helps power Ekata’s Identity Graph.
A distinctive element of Ekata’s data sourcing process is our personal touch. Someone from our data sourcing team, and often myself, travels to meet the data source in person. Always. No matter where they are in the world. Why? Trust.
- We want to trust the people running the businesses that provide the data our products rely on.
- We want to trust the source of that data – something tangible, like voter rolls, utility bills, telco data or the postal service. We don’t trust black boxes.
- We want to trust that the company we are sourcing from has the right to license the data.
We do all these steps because our customers need to trust us, and they need to trust the data in the Identity Graph that is at the foundation of our products.
Trusted data also requires engineering rigor. Ekata’s data engineers use heuristics to extract, match, and resolve identities from incomplete or inaccurate data entities. They put hard-to-standardize global entities such as addresses and names into a standard and consistent format. To ensure the highest quality at the attribute level, they use statistical methods to test, compare, and validate data.
Our data sourcing and ingestion process gets tighter, more granular, and targeted, month over month, quarter over quarter, year over year. Today, I would put our global data sourcing muscle up against any company in the world.
Credit Risk: A Deterministic Approach
Why do I discuss data sourcing and vetting above? Because the question the executive in my story was asking me comes from a credit risk lens. More specifically, since this was in the U.S., the requirements of the Fair Credit Reporting Act (FCRA) on the source of underlying data.
Our data does not originate from the FCRA-specified sources, but it does originate from trusted sources.
If I were applying for a home loan or insurance, in order to properly underwrite me, FCRA requires that the underwriter pinpoints pulling credit history on “the” Rob Eleveld applying. This is completed, as specified by FCRA, by identifying me through matching my Social Security Number (SSN) and date of birth (DoB), along with my name, to a credit header file that originates from one of the three credit bureaus.
In short, assessing credit risk, and specifically the identity verification associated with it, is a deterministic approach consisting of verifying a direct line between a name and a unique identifier (SSN or more broadly a National ID) and DoB. This process is still required by law today for assessing the credit risk of an applicant.
An important point here is that the FCRA was signed into law in 1970, long before electronic commerce, online lending, electronic remittances, and peer-to-peer marketplaces existed. As called out in the law, it was never intended to be used for fraud risk. Instead, it was designed to ensure all U.S. citizens had fair and unbiased access to credit based on objective criteria like credit history. It is hardly a system designed for the requirements of managing global digital fraud risk in 2020!
The Constraints of a Deterministic Approach
Challenges with the deterministic approach become evident when applying the same credit risk methodology to today’s global fraud risk.
- The “static data elements” used for credit risk identity verification have been compromised many times over in the past 50 years. There is a common agreement amongst industry professionals that anyone’s static identity elements of SSN/National ID and DoB can be purchased on the Dark Web, quickly and at scale.
- The approach is siloed country by country since credit bureaus are regulated country by country, and therefore the data is necessarily siloed country by country.
- This credit risk data for deterministic analysis is limited to the 15-20 countries with mature credit markets and associated credit bureaus.
We see additional deterministic methods across the industry today, including such things as:
- Government document scan and upload (passports, driver’s license, etc.)
- Two-factor authentication via a text code to one’s mobile phone
- Biometrics – like one’s fingerprint or an iris scan – both unique identifiers to a single person and static
In short, a deterministic approach is required by law for credit risk. It is also useful for certain high-security requirements (e.g. I am glad iris scan technology is available to help secure an entrance to a nuclear facility!) But, in all cases, a deterministic approach:
- Relies on static data elements which are very vulnerable to compromise, or
- Introduces significant friction – fine for the tightest security but not acceptable for the vast scale of online scenarios.
Fraud Risk: A Probabilistic Approach
Fraud Risk, by contrast, has core business requirements that call for a different approach:
- Fraud Risk is not siloed by country, but is multi-geo across tens of countries or even north of 100 countries for multinational companies or payment service providers (PSPs).
- Fraud Risk requires a much lower friction approach for new account signup, authentication, and authorization. No online customer in any of these scenarios is asked to submit their SSN/National ID.
Most importantly, business executives are not asking for a deterministic solution for digital risk; they are not in search of “the definite answer.” They want to manage fraud down to certain basis points (a tax they know they must pay), because they understand that the lowest fraud basis points lead to a massive cost of false positives on the flip side of that coin.
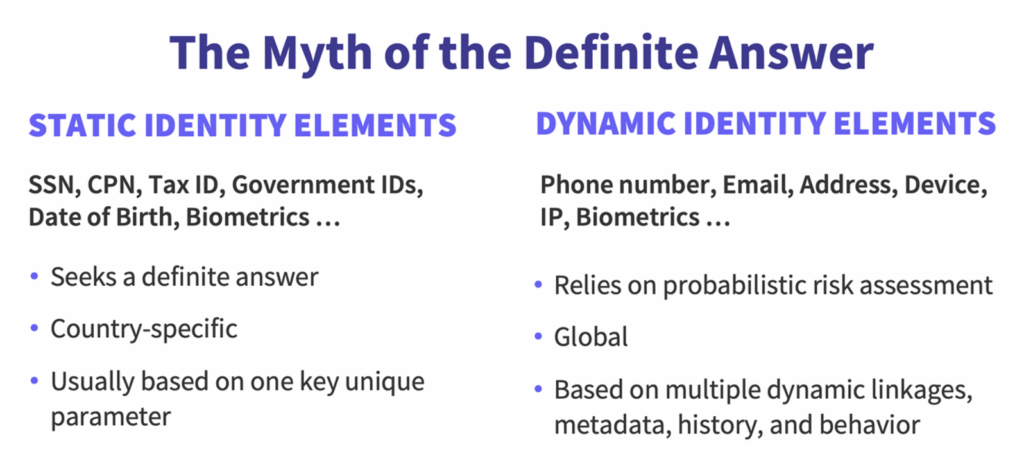
Based on over seven years in the fraud risk market, I fundamentally believe that a probabilistic approach via some combination of machine learning models and rules is much more flexible for the vast majority of digital identity verification use cases.
Advantages of a probabilistic approach include:
- Fraud risk management can be tightened or loosened based on company needs by adjusting rules, retraining models, scaling up or down review, etc.
- Risk signals can be layered to compensate for the common “cold start problems” of no existing data in a new country, or a new product line, or lack of coverage on certain data inputs based on regulatory constraints.
- Models and/or rules can be retrained and adjusted to deal with new scenarios, which we see happening amongst nearly all of our customers right now due to radical changes in volumes, new account signups, and new shopping patterns due to the impacts of COVID-19.
- A probabilistic methodology enables passive authentication by weaving different types of “dynamic data” available in online signup or transaction flow (dynamic PII, behavioral device data like typing patterns, etc.) to authenticate a customer behind the scenes, without introducing friction.
Trusted Data: All Day, Every Day
And so, we come full circle. Credit bureau files constitute trusted data for a credit risk process. But digital fraud risk requires probabilistic analysis. Ekata’s global digital identity verification data, especially our uniquely derived signals like Identity Risk Score, Network Score, and our IP Risk flag, constitute trusted data for probabilistic fraud risk.
Our 1,500+ global customers and partners absolutely trust our data for probabilistic digital identity verification. And most importantly? They trust our team and our company to build enduring customer relationships.
Trust starts at the source.
In the meantime, I invite you to contact one of our representatives to learn more about how Ekata can help your business.



