Overview
Ekata’s Pro Insight is the only global identity review solution that provides six ways to search, robust analytics and admin tools, direct workflow integrations, and a clear and focused user experience. Pro Insight enables organizations to assess identity risk, approve good transactions, and investigate fraud on a global scale.
Pro Insight’s flagship search Identity Review provides a quick comprehensive view of the identity behind a transaction by cross-checking the 5 core digital and traditional data attributes of name, email, phone, address, and IP. Identity Review is the best starting point to assess the risk of the identity behind a transaction and is powered by over 70 data elements from our award-winning Identity Check API and real-time machine learning insights from our Identity Network.
Using Pro Insight for Identity Review
Identity Review returns a Confidence Score, the key signals impacting the score, alerts and match statuses between the 5 core data attributes, and in-depth details for each of these attributes.
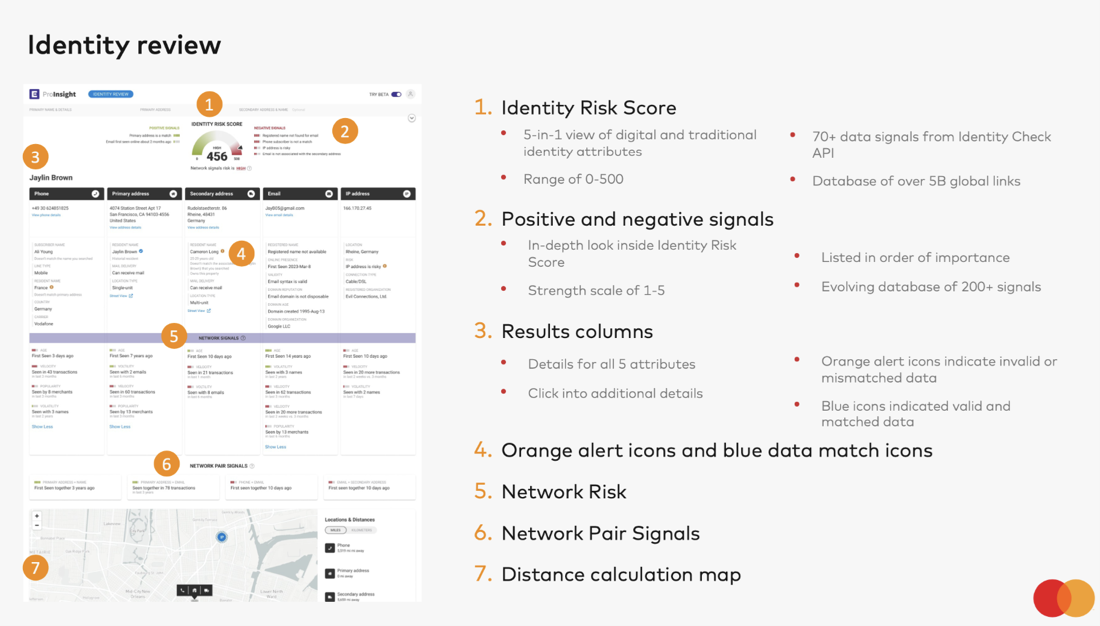
1. Identity Risk Score
At the top of the results panel is the Identity Risk Score which is meant to give you a quick first view of the risk associated with the identity and transaction. The Identity Risk Score provides directional guidance for manual review by taking into consideration all attributes and their relation to one another to produce a score ranging from 0 to 500 with a higher Identity Risk Score indicating a riskier transaction.
2. Risk signals
On each side of the score, you can find positive and negative signals which provide insights into what’s driving the score. These dynamic signals take all transaction inputs into account, are weighted by impact, and listed in order of importance with the strongest signals listed first. The positive signals are listed on the left in green while the negative are listed on the right in red.
3. Results columns
Below the Confidence Score and signals sits the result columns that provide the ability to dive into the individual inputs and links between them: phone, address (primary and secondary), email, and IP. Blue data match icons indicate a data match and orange alert icons indicate a mismatch or invalid input. Additionally, the email, phone, and address columns provide hyperlinks to view additional in-depth details, such as related people, additional phone numbers, and more. For example, when you click “view address details,” you can see address history, associated people, and more.
4. Orange alert and blue data match icons
Mismatched or invalid inputs are marked by an orange alert icon, while valid, matched data are marked by a blue checkmark. See at a glance what core identity attributes (name, phone, email, address, and IP) are flagged as problematic in every manual review.
5. Network Risk
Network Risk is a machine learning prediction, derived from the Ekata Identity Network, that provides insight into how risky a digital interaction is based on activity patterns of core identity elements. It is categorized as either LOW, MEDIUM, or HIGH.
Network Risk Signals then provide context behind the Network Risk score by tracking key behavioral fraud and activity patterns of a consumer:
- Velocity indicates the number of times an identity attribute was seen in recent transactions.
- Example – this phone number has been seen in X transactions over the last 90 days.
- Trend – once a fraudster steals an identity, they may try to commit fraud through multiple transactions at the same time before the identity is flagged.
- Volatility indicates the number of times an attribute of an identity has changed over the last 90 days.
- Example – X phone numbers have been associated with this shipping address in the last 30 days.
- Trend – once a fraudster steals an identity, they may use different combinations of identity attributes to commit fraud.
- Popularity indicates the number of merchants where an attribute is seen in recent transactions.
- Example – this phone number has been seen by X number of different merchants in the last 30 days.
- Trend – once a fraudster steals an identity, they may try to commit fraud with multiple merchants at the same time before the identity is flagged.
- Age measures the reliability of an identity element based on its history in Ekata’s network
- Example – this address and phone number were first seen together 1 day ago
- Trend – fraudsters typically have a shorter, more fragmented history
6. Network Pair Signals
Network Pair Signals describe any combination of the core identity elements, i.e. name, phone, address, email, and IP, and their relationship with each other.
It offers manual review agents context into not only how core identity elements have interacted with each other, but also the length of the association. This provides context into identity elements that are seen for the first time with an address, or those that have been associated for a significant period of time, such as a name and phone seen together by over 15 merchants in the last 3 years.
7. Distance calculation map
At the bottom of the results page is the distance calculation map, an interactive map tool where you can explore distances between different data attributes. Once you click the location you would like as a starting point, you will see distances under the other locations that indicate how far they are from your starting point. You can click different locations to toggle between distance views.
If you have any questions or for more information, contact us at support@ekata.com.
